APF Technologies
Always Protect Files
Stop Data Breaches with Universal Data Shield
A Holistic Quantum-Computing Safe Data-centric Security Solution
Introducing Universal Data Shield – Quantum Safe (UDS-QS), the standard-setting holistic Data-Centric security solution developed to safeguard all data — whether at rest, in transit, or in use — using a patented Quantum-Computing safe encryption scheme. UDS-QS leads the charge in the cyber arms race by eradicating vulnerable data attack surfaces prone to deceptive and impersonation attacks, thus filling the void left by the Zero Trust Architect (ZTA)
High Return of Investment
UDS-QS offers a comprehensive solution that addresses an organization's full spectrum of data security and management requirements, aiming to eliminate vulnerabilities that could lead to future data breaches and prevent the substantial financial and operational losses resulting from such incidents. The return on investment with UDS-QS can be rapidly realized through the consolidation of data protection tools, with further efficiency gains derived from the solution's built-in compliance features that help enterprises align with regulations such as GDPR and HIPAA .
Frictionless Deployment
Simplicity is at the core of the Unified Data Shield – Quantum Safe (UDS-QS) solution. Cloud-native SaaS platform enables turnkey deployment, while patented design aligns with the current security policy standards recommended by the National Security Agency (NSA). UDS-QS removes the complexity typically associated with deploying advanced data protection controls. The lightweight local application seamlessly integrates with existing processes and systems, empowering employees to focus on their work without added burden or disruption.
Future Proof Protection
The transformative capability of the Unified Data Shield – Quantum Safe (UDS-QS) solution is rooted in its innovative encryption methodology. By eschewing vulnerable asymmetric cryptography, which is prone to quantum computing attacks, this unique design employs quantum-computing-resistant cryptographic techniques to secure data at a granular level, providing protection against even the most advanced future threats.
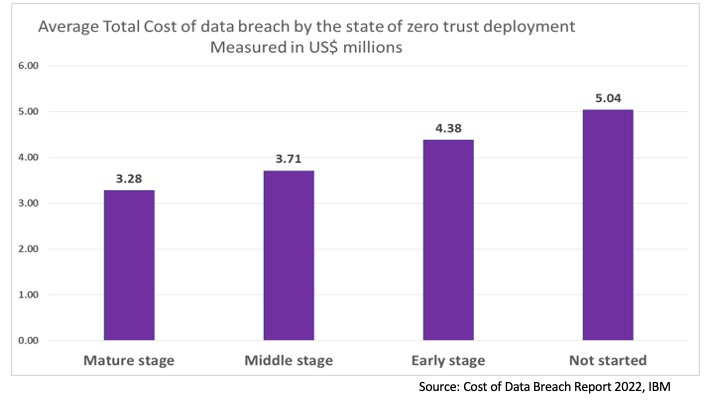
Zero Trust Architecture Is Aging and Data Breaches are Rampant
Every effort to contain data breaches has thus far failed. The latest “Cost of a Data Breach Report” produced by IBM shows that ZTA, which had been heralded as a potential savior, also falls short of preventing data breaches. The IBM stated that 35 percent of reporting companies that had implemented Zero Trust programs experienced an average loss of more than $3.2 million from a data breach.
“The enterprise attack surface is expanding fast and attackers will quickly consider pivoting and targeting assets and vulnerabilities outside of the scope of zero trust architectures (ZTAs),” explained Jeremy D’Hoinne, VP analyst at Gartner.
In other words, ZTA has quickly become a white elephant. Cyber risk is becoming so elevated that Mr. Mario Greco, chief executive at the insurer Zurich, recently told The Financial Times that cyber “will become uninsurable.”
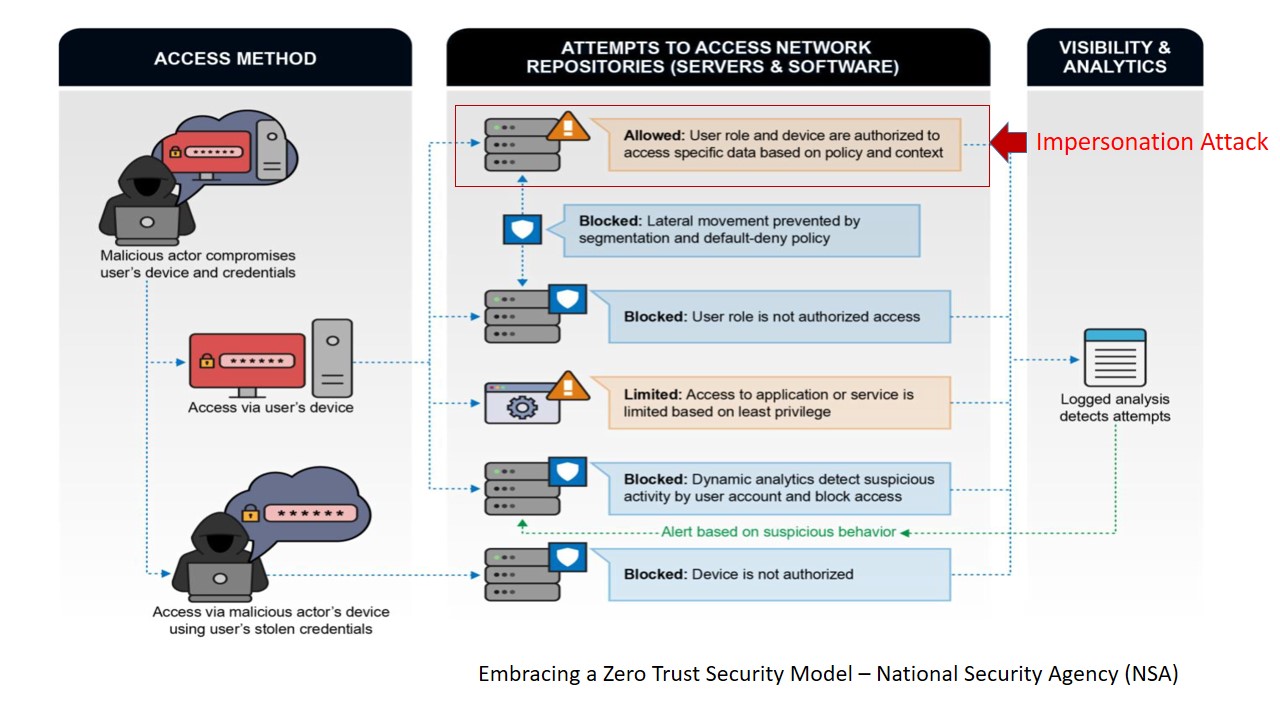
National Security Agency (NSA) Demands A Data-Centric Solution, APF Delivers
The National Security Agency (NSA), with its eyes, ears, and hands in every corner of the cyberspace, proposed a new cybersecurity pardigm. “The Zero Trust security model assumes that a breach is inevitable or has likely already occurred … data-centric security model allows the concept of least-privileged access to be applied for every access decision, allowing or denying access to resources”. The NSA demanded a data-centric solution and APF has delivered. UDS-QS is the first and only Data-Centric security solution incorporating, yet going beyond, Zero Trust Principles
A Holistic Data-Centric Solution Protects Every Data Everywhere All at Once
UDS Protects Every Data
Unlike other products that only protect the data in a storage (like S3 by AWS, Box), or in a network segment (like Hardware Security Module ), UDS-DS is designed to protect every data. Its cloud native and patented quantum safe encryption and key management allow UDS-DS to horizontally expand without limit. UDS-QS’s data discovery and end-to-end protection capability minimize protection for duplicated data.
UDS Protects Data Everywhere
Data moves by nature. Every time a piece of data moves, it needs protection when it is in transit. It also needs to be protected at rest on the new devices because clear data is a new attack surface created. The current solutions require multiple products. UDS, however, protects data seamlessly throughout the entire process in transit and on any devices, by itself. By protecting data seamlessly, UDS-DS leaves zero attack surface along the way.
UDS Protects Data All at Once
Accessing organizational data is a privilege, not a right. By protecting data end-to-end and seamlessly, UDS also ensures a user has to acquire access right from the UDS to the data he needs to access regardless when and where the data resides. Although the unique integration of the UDS app makes this process effortless to the end users, the intelligent access right management by UDS keeps a watchful eye on every data at any time all at once.
Contact Us
Interested in learning more about how APF can help your organization’s data protection and cyber privacy needs?