Wining the cyberwar requires both proactive and reactive defense measures


Wining the cyberwar requires both proactive and reactive defense measures

A successful attack on AES-256 is a black swan, even if it could be so expensive that only a handful of nation states can afford it. What makes a successful attack on AES a black swan are the facts that AES-256 is becoming the foundation of cyber security and we are not prepared for it to be broken at all.

Naturally, many of you have doubts when we say that UDS stops data breaches. It is impossible for one application to do when so many layers of defenses created by combinations of different solutions and software have not made a dent on data breaches, or is it? Repeating the Same And Expecting Different Results […]

In 2023, a single bug in a little-known software caused one of the largest data breaches in history that impacted over 60 million people around the world. Making the matter worse, even if the companies whose data were stolen by the MOVEit attackers used every cyber security technology available, it would have made no difference […]
In its presentation to the Cybersecurity and Infrastructure Security Agency (CISA) of the United States on November 28, APF Technologies LLC (APF) outlined the broad capabilities of its Universal Data Shield (UDS) solution, and how it would deliver an immediate positive impact on the cybersecurity of companies and governmental agencies in the US and around […]

By Joseph F. Norton I recently had the opportunity to speak with the cybersecurity leadership of a very large multi-national organization. My lead-off statement concerning the state of the cybersecurity today was: “Cyberattacks are a hyper-growth industry!” Until we, the cybersecurity practitioners, and the organizations we strive to protect, change the economic returns for bad […]
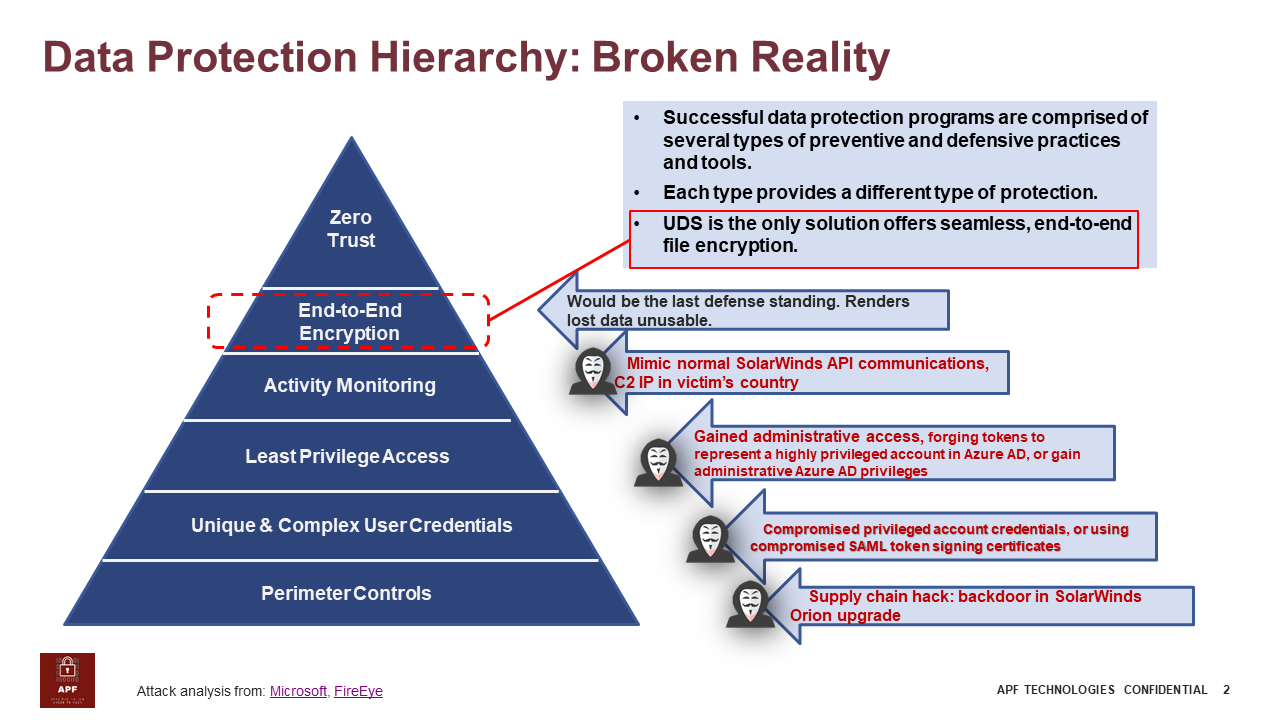
End-to-end data protection is the best answer, if not the only answer at the moment. If you can’t be sure the security of the infrastructure, it is natural that you secure the crown jewels the thieves want: data.

End-to-end data protection is the best answer, if not the only answer at the moment. If you can’t be sure the security of the infrastructure, it is natural that you secure the crown jewels the thieves want: data.