APF Technologies
Always Protect Files
Secure Information With UDS In the aftermath of solarwinds Attack
The supply chain hack sent shock waves through the U.S. government and private sectors. The victim list includes the State Department, the Department of Homeland Security and parts of the Pentagon, and 400 companies from future 500 list are among the 18000 customers that have downloaded the infected software. In-depth analysis of the breach by Microsoft and FireEye reveals the deeply troubling inadequacy of the current cybersecurity infrastructure that is being penetrated and evaded by the attacker since March. In fact, the malware was discovered “almost accidentally” by FireEye, the world’s premier cyber-attack investigation company, through “an automated security alert of employee logging into the company’s virtual private network from an unrecognized device,” which then found itself being hacked. FireEye’s crucial tools that are used to evaluate the client’s cyber defense system were stolen.
In the aftermath of the incident that is called “a moment of reckoning” for the world by Brad Smith, the President of Microsoft, we need to come up with a solution quickly before the next attack happens, or even before the threads from this attack are completed removed which, by some estimate, may take years.
FireEye and Microsoft published details of method of attacks that showed how the attacker eluded all the security measures in place.
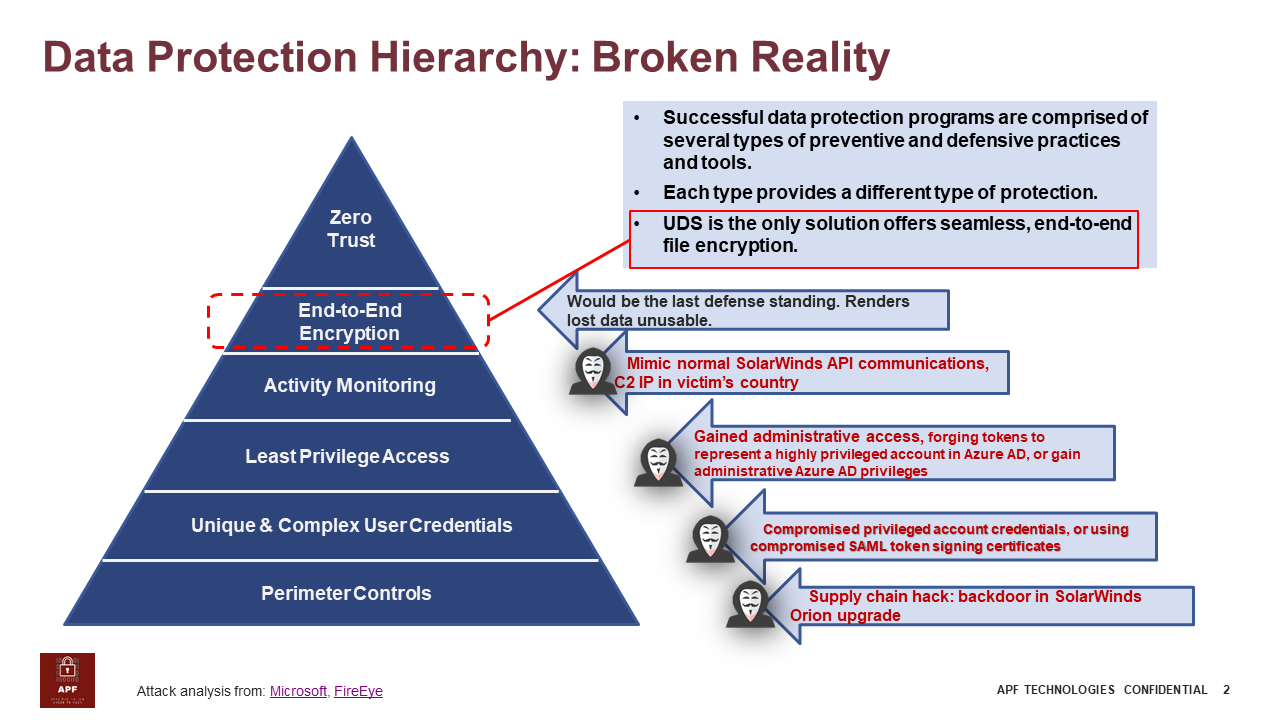
What are broken:
- Perimeter Defense: Anti-virus and firewalls are useless in this supply chain attack. “The embedded backdoor code loads before the legitimate code executes. Organizations are misled into believing that no malicious activity has occurred and that the program or application dependent on the libraries is behaving as expected.”
- Unique & Complex User Credentials: The attacker bypasses the password protection through “either gained administrative access using compromised privileged account credentials (e.g. stolen passwords) or by forging SAML tokens using compromised SAML token signing certificates,” and “leveraging minted SAML tokens to access user files/email or impersonating the Applications or Service Principals by authenticating and obtaining Access Tokens … to access specific users’ emails using the permissions granted to the impersonated Application or Service Principal. In many cases, the targeted users are key IT and security personnel”
- The Least Privilege: attackers obtained administrative or privileged access though stolen password or forging SMAL token, which allow attackers to run malicious code and then cover its track. It also allows that “the actor made modifications to Azure Active Directory settings to facilitate long term access.”
- Network monitoring: The attacker eluded the monitoring by “impersonating existing applications…, the access is hidden amongst normal traffic,” and “mimicking normal SolarWinds API communications,” as well as using “IPs in victim’s country.”
- Application access: the attacker “periodically connects from a server at a VPS provider to access specific users’ emails using the permissions granted to the impersonated Application or Service Principal”
In conclusion, once the back door code is installed onto the system, it was able to break every single security measure and steal data without being noticed. In other words, the current cyber security solutions are not able to stop or detect a sophisticated attack like this.
Stop this attack
The steps recommended by Microsoft to remedy the attach contains 2 parts, although none will be able to stop next attack
- Stop this attack with known knowledge. Virus scan to remove existing malwares found though the investigation, and block traffic to command 2 control host.
- Re-enforce best practices of SAML, certificate protection, monitoring sign in, etc., although no direct evidence was provided that those measures could have stopped this attack.
Prevent the future attack with UDS
- All files are encrypted with strongest possible algorithm and key length with no password or master key to steal.
- Every attempt to access any data by any user is being evaluated through access policies.
- Every access attempt is logged and feed to AI powered user access pattern analysis to detects anomalies and send early warning,
- Even if above measures failed, once user reaches the UDS access limit, UDS stops further data access and sound alarm to prevent mass data breach. There is no way to go around this limit by design.
- Being SaaS service, UDS doesn’t require the overhead to manage. It is flexible and cheap enough to secure every file in the environment.